Media Access Control (MAC) Protocols And Random Access in Data Link Layer (DLL)
Till now we have been assuming that an end to end network (consisting of a source and destination) is nothing but a point to point i.e PPP (dedicated) link . But consider a situation where there is a requirement of a broadcast network (the ideal case with multiple participant hosts like in case of mobile network).
In that case, we have to deal with the Media Access Control (Aloha and CSMA methods) for efficient networking.
Thus we have assumed that there is an available dedicated link (or channel) between the sender and the receiver. Now consider a case where , we use our cell phone to connect to another cellular phone, the channel (the band allocated) is not dedicated (and distributed among many members).
A person standing a few feet away from us may be using the same channel to talk to his/her friend. Thus indeed we require exclusive protocols (in the data link layer) to satisfy this scenario in real life.
What is Media Access Control ?
In a broadcast network, the single communication channel is to be allocated to one transmitting user at a time. The other users connected to this medium should wait. Datalink layer is divided into two functionality-oriented sublayers i.e
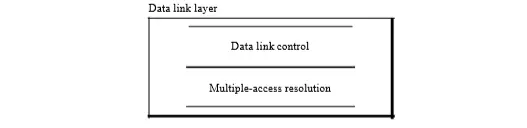
The upper sublayer is basically responsible for the data link control, and the lower sublayer is responsible for resolving the access to the shared media. In the case of a dedicated link (PPP network), there is no need for the lower layer.
When nodes or stations are connected and use a common link, called a broadcast link, we need a multiple access protocol to coordinate access to the link. Let us take the more realistic case.
Consider yourself speaking in an assembly. We don’t want any other person to start speaking at the same time, don’t want anyone else to disturb or interrupt us during our speaking etc. Same issues faced during transmission in a broadcast link.
Thus in order to maintain required efficiency in network, we have to understand specific medium access control (also called as media access control) protocols implemented in DLL .
When a number of stations (users) use a common link of communication system we have to use a multiple access protocol in order to coordinate the access to the common link.
The three techniques used to deal with the multiple access problems are as follows :
- Random Access Method
- Controlled Access
- Channelization
Random Access in Media Access Control (MAC)
In the random access technique, there is no control station. Each station will have the right to use the common medium without any control over it.
With increase in number of stations , there is an increased probability of collision or access conflict. The collisions will occur when more than one user tries to access the common medium simultaneously.
As a result of any possible collision, the packets of data may be modified or destroyed completely. At each instance, any station that has data to send uses a procedure defined by the protocol to make a decision on whether or not to send. This decision further depends on the state of the medium (idle or busy).
Stations compete with one another to access the medium. In the random access method, each station has the right to the medium(channel) without being controlled by any other station. Following are the random access methods:
- Aloha (Pure Aloha)
- Slotted Aloha
- CSMA
- CSMA – CD
- CSMA – CA
Pure Aloha in random access (meaning ‘hello’ in Hawaii)
Its main principle is to allow any station to broadcast at any time. If two signals collide, each station simply waits a random time and try again.
Collisions are easily detected, when the central station receives a frame it sends an acknowledgment on a different frequency .
If a user station receives an acknowledgment it assumes that the transmitted frame was successfully received and if it does get an acknowledgment it assumes that collision had occurred and is ready to retransmit.
It is obvious that we need to resend the frames that have been destroyed during transmission. The pure ALOHA protocol relies mainly on acknowledgments from the receiver.
Pure ALOHA dictates that when the time-out period passes, each station waits a random amount of time before resending its frame. The randomness will help avoid more collisions. We call this time the back-off time i.e Tb .
The time-out period is equal to the maximum possible round-trip propagation delay, which is twice the amount of time required to send a frame between the two most widely separated stations.
Algorithm Used :
- Transmit one frame and wait for the acknowledgment.
- If acknowledgment received (i.e no collision) then go to step 1.
- If acknowledgment not received(i.e collision has occurred) , select a random time (back off time) for frame retransmission.
Let us now understand the concept of vulnerable time in Aloha. Vulnerable time is nothing but a time in which there is a possibility of collision. We assume that the stations send fixed-length frames with each frame taking ‘ Tf ‘ to send. The vulnerable time, which is a duration in which a collision may occur in pure ALOHA, is 2 times the frame transmission time . Let us now understand the Slotted Aloha concept.
Slotted Aloha in Random Access
Slotted Aloha is basically introduced to improve the efficiency of pure aloha. As we have already seen that the pure aloha has a vulnerable time of 2 x Tf . This is because there is basically no rule that defines when the station can send.
In slotted ALOHA we divide the time into slots of ‘Tf’ sec and force the station to send only at the beginning of the time slot. If we consider frame transmission time as ‘T’ .
Collisions occur if any part of two transmission overlaps. Suppose that ‘T’ is time required for one transmission and that two stations must transmit.
The total time required for both stations to do so successfully is 2T. In case of pure ALOHA allowing a station to transmit at arbitrary times can waste time upto 2T.
As an alternative, in the slotted ALOHA method the time is divided into intervals (slots) of ‘ T ‘ units each and require each station to begin each transmission at the beginning of a slot.
In other words, even if the station is ready to send in the middle of a slot, it must wait until the beginning of the next one. In this method a collision occurs when both stations become ready in the same slot.
The vulnerable period has been reduced to half that of pure ALOHA. The slotted ALOHA has a double throughput efficiency than the pure ALOHA system. With increase in the length of the frame or reduction in the propagation time the utilization gets improved.
Carrier Sense Multiple Access (CSMA) in Medium Sharing Technique
The CSMA protocol operates on the principle of carrier sensing. In this protocol. a station first listens to see the presence of transmission (carrier) on the cable and decides to respond accordingly.
The chance of collision can be reduced if any station senses the medium before trying to use it. Carrier sense multiple access (CSMA) requires that each station first listens to the medium (or check the state of the medium) before sending.
In this way the chances of collision can be reduced by sensing the medium before sending any frames in it . The possibility of the collision still exists because of the propagation delay. when a station sends a frame, it still takes time (although very short) for the first bit to reach every station (and for each station to sense it).
Let us now explore the three types of CSMA :
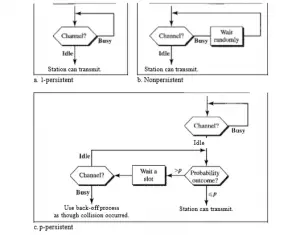
Non·Persistent CSMA : In this scheme, if a station wants to transmit a frame and it finds that the channel is busy (some other station is transmitting) then it will wait for a fixed interval of time. After this time, it again checks the status of the channel and if the channel is free it will transmit.
Persistent CSMA : In this scheme the station which wants to transmit, continuously monitors the channel until it is idle and then transmits immediately. The disadvantage of this strategy is that if two stations are waiting then they will transmit simultaneously and collision will take place. This will then require retransmission.
P – Persistent CSMA : The possibility of such collisions and retransmissions is reduced in the p·persistent CSMA. In this scheme, all the waiting stations are not allowed to transmit simultaneously as soon as the channel becomes idle . A station is assumed to be transmitting with a probability “p”. For example if p = 1/5 and if 5 stations are waiting then on an average only one station will transmit and others will wait .
Carrier Sense Multiple Access/Collision Detection (CSMA/CD)
The problem in CSMA explained earlier is that a transmitting station continues to transmit its frame even though a collision occurs.
The channel time is wasted due to this. In CSMA/CD, if a station receives other transmissions when it is transmitting, then a particular collision can be detected.
The CSMA method doesn’t specify the procedure following a collision. Carrier sense multiple access with collision detection (CSMA/CD) enhance the algorithm to handle the collision.
In this method, a station first monitors the medium after it sends a frame to see if the transmission was successful. If so, the station is finished. If there is any collision, the frame is sent again.
As soon as a collision is detected, the transmitting stations release a jam signal. The jam signal will alert the other stations. The stations then are not supposed to transmit immediately after the collision has occurred.
After some “back off” delay time the stations will again retry the transmission. If again the collision takes place then the backoff time is increased further.
For CSMA/CD to work, we need a specific restriction on the frame size. Before sending the last bit of any frame, the sending station must detect a collision, if any and then it abort the transmission.
Carrier Sense Multiple Access/Collision Avoidance (CSMA/CA)
We need to avoid collisions in the case of wireless networks because they cannot be detected. Carrier sense multiple access with collision avoidance (CSMA/CA) was introduced for this network. Collisions are avoided through the use of CSMA/CA’s three strategies i.e. the interframe space, the contention window, and the acknowledgments.
When there is a collision, the station receives two signals i.e. its own signal and the signal is transmitted by a second station. To distinguish between these two cases, the received signals in these two cases have to be significantly different.
Finally we have reached the end of this long post. Hope you enjoyed it. Stay tuned for more stuff ..

Aric is a tech enthusiast , who love to write about the tech related products and ‘How To’ blogs . IT Engineer by profession , right now working in the Automation field in a Software product company . The other hobbies includes singing , trekking and writing blogs .