What Is Data Encryption Standard (DES) In Cryptography ?
Data Encryption Standard (DES) is a block cipher published by National Institute of Standards and Technology (NIST). DES was originally developed by an IBM team formed in early 1970 in response to a customer request for a method to secure data. This draft was initially rejected because of small key length (56-bits), which could make ciphertext weaker to many attacks.
Later NIST published DES in January 1977 and defines DES as the standard for use in unclassified applications . The day onwards DES has been proven the most widely used symmetric key cryptographic algorithm.
What Is Data Encryption Standard (DES) ?
Data encryption standard takes 64-bit plaintext as an input and creates 64-bit Ciphertext i.e. it encrypts data in block of size 64-bits per block. Divide plaintext message into 64-bit block each. In simple terms , in DES the given plaintext message is divided into size 64-bits block each and encrypted using 56-bit key at the initial level.
At the decryption side, DES takes 64-bit ciphertext and creates 64-bit plaintext and 56-bit key .
The principle of DES is very simple. Divide plaintext message into block of size 64-bits each, which is initial permutation. After initial permutation on 64-bit block, the block is divided into two halves of 32-bit called left plaintext and right plaintext.
The left plaintext and right plaintext goes through 16 rounds of encryption process along with 16 different keys for each round. 16 rounds of encryption process left plaintext and right plaintext gets combined and final permutation is performed on these combined blocks.
What Is Initial Permutation In Data Encryption Standard (DES) ?
An initial permutation is a process of rearranging or shuffling each bit of original plaintext block with any other random bit of same plaintext message block.
For example : First bit of original plaintext block replace with 48th bit of original plaintext block, the 2nd bit replaces with 57th bit of original plaintext message .
This process called jugglery of bit position of plaintext block which is applied to all original plaintext blocks in a sequence.
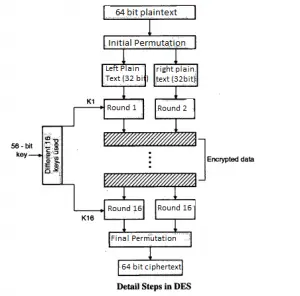
After initial permutation the 64-bit plaintext block get divided into two halves LPT (32-bit) and RPT (32-bit).
Now 16 rounds of encryption process were completed on LPT and RPT.
How Final Permutation Takes Place In DES ?
The last operation a data encryption standard is a permutation of 32-bit LPT and 32-bit , RPT produced from XOR and swapping process. Final permutation was performed after the successful completion of 16 rounds.
Inverse of initial permutation is also called final permutation. This produces 64-bit encrypted block. In this way, all the plaintext gets encrypted by performing broad level steps on it in order to produced encrypted ciphertext.
What The Advantages Of Data Encryption Standard (Strength Of DES) ?
It makes Brute force attack impractical as it use 56 keys so there is the use of 56-bit keys in encryption there are 2^56 (2 raised to 56) possible keys which makes Brute Force attack impractical.
The nature of algorithm: Cryptanalyst can perform cryptanalysis by exploiting the characteristic of the DES algorithm but no one has succeeded in finding out the weakness.
DES is more suitable for the video encryption standards. A machine performing one DES encryption per microsecond would take more than a thousand-year to break the cipher. If a small change in either plaintext or the key, the ciphertext should change markedly.
What Is Double Data Encryption Standard (DES) ?
Double performs the same operation as DES only difference is that double DES uses two keys K1 and K2. First, it perform encryption on plaintext which is encrypted using K1 obtains the first ciphertext again this ciphertext is encrypted by using another key called K2 and converted into final ciphertext.
Mathematically Double DES is represented as
Pt => EK1(Pt) => TEMP = EK1(Pt) => EK2(E(K1(P))) Cp = EK2(E(Kl(Pt)))
Where Pt = Plaintext
EK1(Pt) = Encrypted plaintext with Key K1
TEMP = EK1(Pt) = Temporary Variable to store results
EK2(E(K1(P))) = Encrypted Results of first step using K2
Cp = Final Ciphertext
Decryption of Double DES is the reverse of Encryption. Whatever the ciphertext obtained after the double DES encryption process gets decrypted using K2 and obtain the first ciphertext, the result of the previous step (ciphertext) decrypted using K1 which yields the original plaintext.
To decrypt the cipher text Cp and obtain the plain text Pt Double DES need to perform the following operation :
Pt = DK2 (DK1(Cp))
What Is Triple Data Encryption Standard (DES) ?
Triple DES performs the same operation as double DES only difference is that triple DES uses three keys K1, K2 and K3 while encrypting the plaintext.
First it perform encryption on plaintext which is encrypted using K1 obtains the first ciphertext again this ciphertext is encrypted by using another key called K2 which obtains the second ciphertext which is again encrypted using K3 and converted into final ciphertext Cp.
Mathematically, Double DES is represented as,
Pt => EK1(Pt) => TEMP = EK1(Pt) =>EK2(E(K1(P))) =>EK3 (EK2(EK1(Pt)))
Cp = EK3 (EK2(EK1(Pt)))
Where Pt = Plaintext
EK1(Pt) = Encrypted plaintext with Key Kl
TEMP = EKl(Pt) = Temporary Variable to store results
EK2(E(K1(P))) = Encrypted Results of first ciphertext using Kl
EK3 (EK2(EKl(Pt))) = Encrypted Results of second step using K2
Cp = EK3 (EK2(EKl(Pt))) Final ciphertext encrypted using Kl, K2 and K3
Decryption of Triple DES is reverse of Encryption. The final ciphertext obtained after Triple DES encryption process get decrypted using K3 which results in the second ciphertext, second ciphertext decrypted using K2 which results first ciphertext, first ciphertext again decrypted using Kl which generate the original plaintext Pt.
To decrypt the cipher text Cp and obtain the plain text Pt , we need to perform following
operation.
Pt = DK3(DK2 (DK1(Cp)))
What Are The Possible Attacks In DES Type Of Encryption ?
There are mainly two types of attacks possible in any data encryption standard (DES) mode of encryption . They are as follows :
The first is the Brute Force Attack:
In Brute force attack, cryptanalyst attempt to use all possible permutations and combinations on cipher text message to obtain corresponding plain text message.
This attack trying every possible key until the correct translation of cipher text into plain text message is obtained. It is most often used in a known plaintext or ciphertext only attack. As discussed earlier DES encrypts the block of data using 56 bit key.
Now a day it is very easy to crack the encryption key using specialized hardware called Electronic Frontier Foundation’s Deep Crack.
Second attack is the Meet-in-the-Middle Attack :
This attack was introduced by Markle and Hellman. Meet-in-the-middle attacks can be used against cryptographic algorithms that use multiple keys for encryption. An example of a successful meet-in-the-middle attack is the attack against Double DES.
In order to improve the strength of 56 bit DES algorithm double DES concept was introduced having 112-bit key length and two rounds of DES encryption performed as well but still, it is vulnerable against attack called Meet-in-the Middle.
In meeting in the middle attack, the cryptanalyst has access to both plaintext message and its corresponding cipher text message.
Hope you really liked this post about DES . Stay tuned for more interesting stuff in this series .

Aric is a tech enthusiast , who love to write about the tech related products and ‘How To’ blogs . IT Engineer by profession , right now working in the Automation field in a Software product company . The other hobbies includes singing , trekking and writing blogs .




