Computer Network – OSI Model (OSI Layers Complete Overview )
Howdy fellas!!
You might already go through my previous post about various layered tasks involved in a layered architecture of a network transmission model.
Based upon this understanding we can now proceed further to understand the first reference model based upon the layered architecture concept i.e. Open System Interconnection (OSI) reference model.
An OSI model is based upon the layered framework that allows communication across all types of computer system.
As the use of computer networks can be traced all over the world,thus there should be some standard framework to make worldwide data communication compatible to each other. This standard is developed by the ‘International organization of standardization (ISO)‘ .
This standard framework is called the ‘Model for Open System Interconnection (OSI)’ layer. The complete functionality of network communication (internet and intranet) can be represented using multiple layers. This layered architecture is called OSI reference model.
| layer 7 | Application Layer |
| layer 6 | Presentation Layer |
| layer 5 | Session Layer |
| layer 4 | Transport Layer |
| layer 3 | Network Layer |
| layer 2 | Data Link Layer |
| layer 1 | Physical Layer |
If you are in hurry, you may directly scroll down the page to see brief overview of the functions performed by each of these layers listed. And if you want a detailed overview of each layer , then be patient and enjoy reading..All the applications need not use all the seven layers listed above.
The lower three layers are enough for most of the applications.Each layer is supposed to handle message or data from the layers which are immediately above or below it.
Thus each layer takes data from the adjacent layer, handles it according to these rules, and then passes the processed data to the next layer on the other side. Without wasting much time lets see functions of each layer one by one :
1. Physical Layer
Functions of the physical layer are as follows:
To activate, maintain, and deactivate the physical connection.
The physical layer basically defines the characteristics of the interface between the devices and the transmission medium. It also defines the type of transmission medium
To define voltage and data rates needed for transmission.
Data Rate : The transmission rate is the number of bits sent each second in the physical layer medium.
To convert the digital data bits into an electrical signal.
Representation of bits : The physical layer data consists of a stream of bits (sequence of Os or 1s) with no interpretation.
Synchronization of bits : The sender and receiver not only must use the same bit rate but also must be synchronized at the bit level.
Transmission mode : Physical layer also decides whether the transmission is simplex, half-duplex or full-duplex.
A physical layer does not perform the following operations:
It does not decide the medium or modulation.
In simple words, we can say that the physical layer mainly deals with the interface between two communication devices and converts the message into bits and bits into message (line coding) .
Further deals in the selection of line code, voltage levels, control signals , types of wire and type of connectors used.
The example of the physical layer protocols are RS -232 or RS-449 standards.
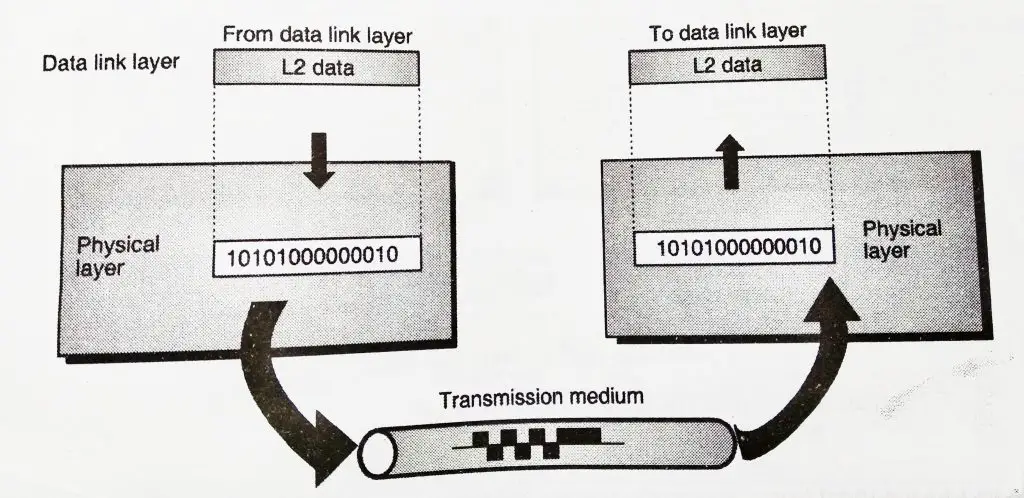
2. Data Link Layer
Functions of the data link layer are synchronization and error control for the information which is to be transmitted over the physical link.
Flow control: If the rate at which the data is absorbed by the receiver is somewhat less than the rate at which data are produced in the sender, then the data link layer imposes a flow control mechanism.
In order to enable the error detection ,it adds error detection bits to the data which is to be transmitted.
Access control : When two or more devices are connected to the same link, data link layer protocols are important to determine which device should have control over the network at any given time.
The encoded data is then passed to the physical layer.The data link layer adds reliability to the physical layer by adding mechanisms to detect and re-transmit damaged or lost frames.
These error detection bits are used by the data link layer on the other side to detect and correct the errors.
At this level, the outgoing message is assembled into frames,and the system waits for the acknowledgments to be received after every frame transmitted.
Physical addressing : If frames are to be distributed to different systems on the network, the data link layer adds a header to the frame to define the sender and/or receiver of the frame.
Finally we can summarize the main functions of the Data Link Layer as frame generation,link establishment, frame transfer and link termination between two hosts.Error and Flow control is also the main features of this layer.
Correct operation of the data link layer ensures reliable transmission of each message.Examples of data link layer protocols are HDLC , SDLC and X.25 protocols.
3. Network Layer
The functions of the network layer are as follows:
To help route the signals through various channels to the other end. The connecting devices (called routers and switches) route or switch the packets to their final destination.
The network layer is mainly responsible for the source-to-destination delivery of a packet, possibly across multiple networks (links).
To act as a network controller by deciding which route data should take .
Logical addressing: The physical addressing implemented by the data link layer normally handles the addressing problem locally.
To divide the outgoing message into packets and to assemble incoming packets into messages for the higher levels.
The main function of this layer is to convert the logical address into a physical machine address.
Also it decides the priority of the message and the route a message packet will take , when they’re present multiple routes to propagate. Further it breaks the large data packets into smaller ones, so that it will comfortably pass through the data link layer.
In short the network layer acts as a network controller for routing data.t helps in the generation of IP packets and facilitates the switching of packets. Routers and gateways form an integral part in this layer.
4. Transport Layer
As the name suggests these layer provides the transport services.The functions of the transport layer are as follows:
It simply decides if the data transmission should take place on parallel paths or single path.
Segmentation and reassembly : A message is divided into transmittable segments, with each segment containing a sequence number. These numbers then enable the transport layer to reassemble the message correctly upon arriving at the destination and to identify and replace the packets that were lost in transmission
It does functions such as multiplexing, splitting or segmenting on the data.
Transport layers guarantees the transmission of data from one end to other.
Like the data link layer, the transport layer is also responsible for error control. However, error control at this layer is performed process-to process rather than across a single link(to avoid duplication, loss and damage ofdata packets). Also, there is flow control(end to end) provided by this layer.
It breaks the data group into smaller units so that they are handled more efficiently by the network layer.
This layer can able to make a connectionless and connection-oriented transfer of data.The transport layer, on the other hand, ensures that the whole message arrives intact and in order, overseeing both error control and flow control at the source-to-destination level(including congestion control for switching center).
Also helps in TCP segment and UDP datagram generation.
5. Session Layer
This layer manages and synchronizes conversations between two different applications.This is the level at which the user will establish a system to system connection.
The session layer mainly allows two systems to enter into a dialog. It further allows the communication between two processes to take place in either half-duplex (one way at a time) or full-duplex (two ways at a time) mode.
It controls logging on and off ,user identification ,billing and session management.
The session layer also allows a process to add checkpoints, or synchronization points, to a stream of data.
In the transmission of data from one system to the other,at session layer streams of data are marked and re-synchronized properly so that the ends of messages are not cut prematurely and data loss is avoided.
In a nutshell , this layer basically helps in Dialog control (for initiating data communication) and Dialog separation(to avoid collision of data)
6. Presentation Layer
The presentation layer makes it sure that the information is delivered in such a form that the receiving system will understand and use it.
It facilitates data encryption and decryption(for source and destination).
The form and syntax(language)of the two communicating systems can be different Examples ,one system is using the ASCII code for file transfer and the other one uses IBM’s EBCDIC.
Under such conditions, the presentation layer provides the “translation “from ASCII to EBCDIC and vice versa.
The presentation layer at the sender basically changes the information from its sender-dependent format into a common format. The presentation layer at the receiving machine then changes the common format into its receiver-dependent format.
It also provides data compression techniques for reducing the number of bits and it is also essential for transmission of multimedia such as text ,audio etc.
7. Application Layer
Application layer is at the top of all the layers.It provides different services such as manipulation of information in various ways , transferring the files of information, distributing the results etc. to the user who is sitting above this layer.
The functions such as LOGIN ,or password checking are also performed by the application layer. Electronicail , accessing WWW,internet telephony etc are some of its main functions.
It provides user interfaces and support for the services such as the electronic mail, remote file access and transfer, shared database management, and other types of distributed information services.
A network virtual terminal is a software version of a physical terminal, and it mainly allows a user to log on to a remote host. The user can log on to a remote host due to this arrangement.
The application layer provides File Transfer Access and Management (FTAM) which allows user to access , retrieve , manage or control files in a remote computer.
We almost covered a brief introduction about each OSI layer. So now we will see some of the merits and demerits of OSI Reference Model :
Firstly we will see the merits :
- It is a general model.It supports both connectionless and connection oriented services.
- The protocols used in OSI model can be easily substituted by new protocols as technology changes.
Some demerits:
- As this model was proposed before the protocols were invented , so in real life, there is a problem of fitting protocols into a model.
- Session and presentation layers are typically not of much use .
For a quick reference guide , you may refer the below table :
| Summary of Layers | ||
| layer 7 | Application Layer | To allow access to network resources LOGIN and password checking etc |
| layer 6 | Presentation Layer | To translate, encrypt, and compress data |
| layer 5 | Session Layer | To establish, manage, and terminate sessions helps in synchronization of conversation between two devices |
| layer 4 | Transport Layer | To provide a reliable process-to process message delivery and error recovery , multiplexing ,splitting or segmenting the data , to break data into smaller units |
| layer 3 | Network Layer | To move packets from source to destination, to provide internetworking, routing of signals |
| layer 2 | Data Link Layer | To organize bits into frames, to provide hop-to-hop delivery error detection and correction. |
| layer 1 | Physical Layer | To transmit bits over a medium to provide mechanical and electrical specifications . To make or break any connection. |
Each layer will handle data or message from the layers which are immediately above or below it. For this to happen there are a set of protocols to be followed. All the layers we will see in complete detail in subsequent posts.
Last but not the least, we can say that the purpose of the OSI model is to represent how to facilitate communication between different devices without requiring changes to the logic of the underlying hardware and software.
The OSI model is not a protocol but it is a model for understanding and designing a network architecture that is flexible, robust, and efficient.
In the next post we will see the layers in the TCP/IP protocol suite that do not exactly match those in the OSI model. The original TCP/IP protocol suite was defined as having the four layers i.e. host-to-network, internet, transport, and application. See you soon in my next post ….

Aric is a tech enthusiast , who love to write about the tech related products and ‘How To’ blogs . IT Engineer by profession , right now working in the Automation field in a Software product company . The other hobbies includes singing , trekking and writing blogs .




