The Ultimate Guide To Endpoint Security !! (Why Endpoint Protection Is So Important For Your Organization ?)
Today there are indispensable aspects of digitization that can be seen in every field and in any organization . In other words , the growth and optimal use of resources, all can be correlated to the main factor that is how quickly any particular business entity (MNC/company/or any other organization) adapt to the advanced digital automation and computing strategies.
In this post we will dig deep into the field of Endpoint security , which is indeed a vital factor ensuring to safeguard any organization from cyber threats by means of various Endpoint protection tools .

Why There Is A Need Of Endpoint Security ?
Organizations today are empowered with digitization, and technology has been excessively leveraged to help users connect to the internet for various purposes. However, the questions that need to be asked are:
Are businesses that are online, safe from cyber threats and security breaches ? Are applications and operating systems updated with the latest security patch fixes beforehand or on time ?
This post on Endpoint Security will help you understand the significance of protecting endpoint devices by means of the Endpoint protection tools and software .
So the need of Endpoint security is basically to protect your IT infrastructure from lethal attacks of any Ransomware, Viruses , Malware etc .
Don’t confuse this with any other Antivirus solution , rather the Endpoint security architecture detects potential threats by using intensive AI powered data , series of Fuzzy Logics , continuous monitoring of any suspicious behavior of any code .

So an Endpoint Security precisely provides more enhanced and advanced protection against any malicious patterns for your devices (unlike any Antivirus which normally uses the signature based detection techniques for known patterns of threats) .
Endpoint protection further includes the Sandbox technology that can be used in sync with the cloud database for any application .
What Is Endpoint Security ? (Definition Of Endpoint Security !!)
First, we need to understand the meaning of ‘endpoint‘ in any IT network infrastructure. An endpoint can be defined as a remote computing device that communicates back and forth with a network, to which is it connected.
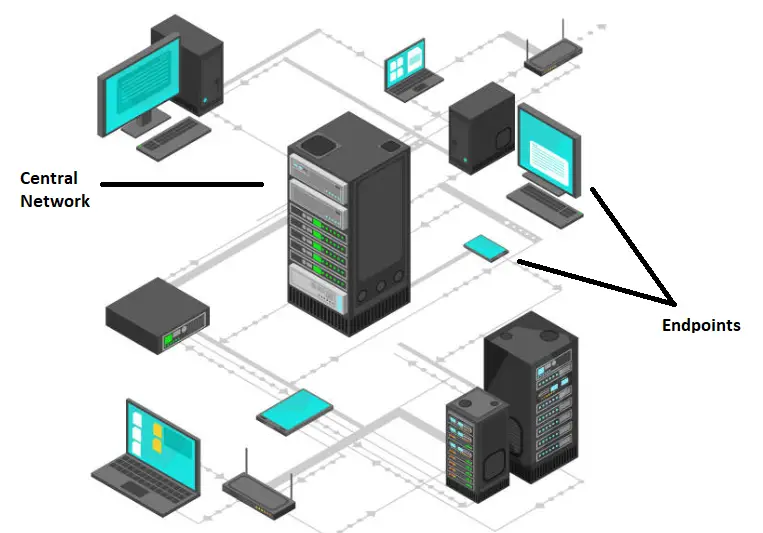
These devices are usually placed outside the organization’s firewall, on the edge of the network through which individuals connect to the central network. Hence, “endpoints” refer to the endpoints of a network (ex desktop, laptops , mobile, or any IoT enabled devices ).
Note : Consider your IT network as a digital perimeter , the larger the devices connect to the network , the bigger the digital perimeter will become , so more gateways will be formed for each device in the network and more points hackers will get to penetrate malicious attacks to your digital assets .

Endpoints present key vulnerable points of entry to perpetrators. Endpoints include assets that can be encrypted, exfiltrated, or leveraged, hence they are attractive targets for attackers to execute code, and exploit vulnerabilities.
Endpoints are increasingly susceptible to cyber attacks as,Organizational workforces are becoming more mobile. Users connect to internal resources from off-premise endpoints all over the world .
So in layman terms we can say that Endpoint Security is an approach to secure the network infrastructure devices that are remotely connected to the client’s devices. It basically ensures a IT security solutions to secure all connected devices from a centralized location. It furnishes consistent protection for your whole IT network .
For any corporate firm , it basically means to protect IT network against any cyber-attacks by focusing on network devices (endpoints) by monitoring their status, activities, software, authorization and authentication .
Each Endpoint Provides The Following Target Areas For The Hackers !!
Objectives for targeting endpoints include, but are not limited to:
1. Identifying and exploiting vulnerabilities in the system.
2. Compromising control of the device to execute an attack. For example, executing a DoS attack with the help of botnets.
3. Using the endpoint as an entry point to an organization, to exploit valuable assets and sensitive information.
Each attack can severely impact your company revenue , led to network downtime , theft of data assets , reputation damage , revenue loss etc .
Even the most efficient cybersecurity solutions in the industry are prone to vulnerabilities and security loopholes.
Endpoint security solutions aim to protect the endpoints connected to a network, from vulnerable malicious threats. It provides a centralized method to protect the IT network by evaluating an organization’s endpoints like desktops, smartphones, laptops, and IoT devices.
Moreover, the current trends in Bring Your Own Device (BYOD) practices, and the ever-increasing threats to mobile devices, further emphasize the need for effective endpoint security solutions.
Difference between Endpoint Security And Antivirus Software !! (Endpoint Security vs Antivirus Head To Head)
Endpoint security is a centrally managed solution that safeguards networks and all their endpoints against threats, with the help of various security tools. More precisely, endpoint security solutions leverage a client/server model to protect various endpoints.
Typically, antivirus is a single program responsible for scanning, detecting and removing malware, spyware, adware, ransomware, and other such malicious entities. Anti-virus solutions are installed on individual devices such as desktops, laptops, smartphones, and on servers.
They run in the background and periodically scan device directories and files for malicious patterns, indicating the presence of malware. The software utilizes its database of virus definitions and signatures to analyze if there are executable malicious codes within it.

Endpoint Security Vs Network Security !!
Endpoint security aims at securing enterprise endpoints, and the enterprise against various security threats.
Network security focuses on the security aspects of protecting the entire network (the whole IT infrastructure) against various security threats. In the nutshell :
- Endpoint security – Securing endpoints
- Network security – Securing the network
Network security protects all inbound variables to hosts, servers, and other important assets. Network monitoring provides a picture of threats evolving over time, encouraging the maintenance of up-to-date situational awareness.
If a suspicious program is found in the network, the network is inspected until a weakness is found.
Network security may be easier to deploy, it does not provide the same level of protection as Endpoint Security.As devices become more mobile, the traffic is not necessarily routed through the business network.
By recognizing endpoints as the new network perimeter, enterprises can prevent external infections from being transmitted into the network.
Also, in many cases, it is easier to detect suspicious code on an end-user device. Analyzing code coming into a network might involve decoding packets that may be disguised as legitimate traffic.
Endpoint Security And Firewall Protection !!
1. Firewalls are responsible for filtering the traffic flowing in and out of a network based on ‘a set of security rules’.
2. On the other hand, endpoint security is concerned not only with network filtering, but also involves other tasks such as patching, logging, monitoring, and so on.
3. Hence, firewalls are also a crucial part of endpoint security just like anti-virus solutions.
4. Though the number of devices protected and the model adopted (client/server) differ, the objective remains the same.
Endpoint Security And Endpoint Protection – Is Both Are Similar ?
The concept behind endpoint security and endpoint protection are almost the same, with one subtle difference.
Endpoint security usually refers to an on premise solution.An on-premise solution is a solution which has to be installed on the network for deployment
Endpoint Protection refers to a cloud based solution.A cloud-based solution is one that is available in the cloud, and enterprises have to subscribe to it.
Features To Look For In Any Endpoint Security Solution !!
There are some top attributes you should look for before you invest in any Endpoint security tool . You may check for the below-mentioned features :
1. Centralised Security Management Portal
Managing thousands of devices, computers and other terminals is not an easy task and involves a lot of effort and coordination. An integrated and robust security solution is essential to avoid redundancy, inconsistencies, and human errors.
Hence, a centralized security management system is needed to manage and control the integrity of the network and endpoint devices.
Desired Properties
- User friendly features
- Lesser security issues
- Affordable
- Instant response in case of suspicious interference
2. Complete Device and OS Protection
Many organizations encourage BYOD, while the new trend emerging is “Choose Your Own Device (CYOD)”. Hence, an organization’s network encompasses various devices operating different operating systems.
Thus, there is a need to refine endpoint security systems to safeguard the functioning and performance of the network under scrutiny.
3. Data Security
An efficient data protection system is vital to complete an endpoint security strategy. Access control mechanisms need to be implemented to enforce authorization and authentication of endpoints as a means to ensure data confidentiality and integrity.
Organizations must ensure:
- Segregation of Network
- Encryption of Data
- Prevention Data Loss
- Controlling File Integrity
- Monitoring Data access
- Protection of Assets
4. Well defined policies and procedures need to be set, as these form the foundation of an organization’s security culture.
It is not only important to have a thorough understanding of what the risks are and how to identify them, but it is equally important for individuals to understand the important role that they play in securing the organization’s data.
Increased vigilance: Staying up-to-date on threats and attacks is the first step towards preventing them from becoming a reality
5. Mobile Threat Management
Securing mobile devices from security threats is a very important aspect of Endpoint Security. Management systems to manage and stand up to threats are crucial to safeguard endpoints.The mobile threat management system must have the following features:
- Effective Validation of Devices
- Managing third-party Content
- Containerization of Mobile Apps
- Penetration Testing
6. Continuous Detection
Detect changes as quickly as possible. Continuous detection as part of Endpoint Security should involve real-time monitoring of network topology, connections and traffic flow.
Expectations
- Mitigate threats across the cyber kill chain.
- Detect changes that pose a potential threat to the organization’s security.
- Identify abnormal behavior and other indicators that reveal a malicious presence in the network.
7. Remediate Incidents
An integrated security management tool should be included in endpoints to ensure the remediation of incidents at the earliest.
An efficient cybersecurity incident remediation process starts with identifying and collecting as much information about it, as possible.
The information gathered must then be analyzed thoroughly to determine the type of threat that is being dealt with, and the potential impact.
Endpoint Security Solutions (Endpoint Security Tools !!)
The days of simple cyber security solutions are far from over. Presently, Endpoint Security tools are expected to thwart threats, different kinds that are now in the open, by preventing them from infecting computers, including mobile devices, virtual desktops, laptops, and workstations.

Presently, there are numerous sophisticated endpoint detection and response (EDR) tools, all professing the detection and prevention of the most subtle attacks.
However, the most effective tools examine these threats through a larger perspective, including the best aspects from network intrusion detection systems, and evaluating the individual process level on each system.
Let us now see some renowned Endpoint security solutions available :
| Product Name | Delivery Form For Server | Endpoints Agents |
|---|---|---|
| Comodo Advanced Endpoint Protection | Windows server or SaaS | Windows (XP SP 3, Vista, Server, 7, 8, 10), Mac , iOS, Android |
| CounterTack Sentinel | CentOS-based server | Windows (XP SP 3, Server, 7 SP 1, 10), Linux |
| CrowdStrike Falcon Host | SaaS | Windows, Mac, Linux |
Endpoint Security – Final Wrap Up !!
An effective and efficient mechanism to secure endpoints and networks requires a strict endpoint security system, which is a security-laden protocol.
Hence, there is a need for an intact strategy that includes well-defined protocols and rules that the devices need to be compliant with. Two primary attack vectors are exploited to compromise endpoints:
- Malicious executables (malware)
- Vulnerability exploits
Effective endpoint security solutions (products or technologies), must prevent malware and exploits (known and unknown variants) from compromising endpoints and servers. An antivirus and a firewall are not enough to protect any corporate-owned or BYOD devices.
A multi-layered approach is required to efficiently protect the devices connected to a corporate network. Hope you really liked this post . Stay tuned for more interesting stuff in this series.

Aric is a tech enthusiast , who love to write about the tech related products and ‘How To’ blogs . IT Engineer by profession , right now working in the Automation field in a Software product company . The other hobbies includes singing , trekking and writing blogs .




