Everything About The Firewall Mechanism (Firewall Types ,Configuration And Security) !!
Have you ever noticed that whenever we tried to install any external software or connect any device to our Mac or Windows computer , we get a message to turn off the inbuilt firewall in order to get that software installed. Also while activating any third party Antivirus , we are supposed to turn off the firewall of our system (any Antivirus already has an inbuilt firewall mechanism) .
So what exactly is this firewall meant for? In this post, we will explore the various types of firewall and their configuration in detail. Just relax and proceed further to know about this protective shield built inside your system.
What Is A Firewall In Any System And What Is It’s Significance ?
A firewall device filters all traffic between the intranet and extranet. All the traffic runs through firewall. The main purpose of the firewall is to keep attackers outside the protected environment. For that policies are set in the firewall to decide what is allowed and what is not allowed.

Moreover, we can decide the allowed places, allowed users, allowed sites, can provide different access rights to a different categories of the users. Ex. Cyberoam through which only educational sites are allowed through college
internet and non-educational sites Like Facebook, Twitter can be blocked.
A firewall is a kind of reference monitor. All network traffic passes through the firewall. That’s why it is always in invoked condition.
A firewall is kept isolated and cannot be modified by anybody other than the administrator. Generally, it is implemented on a separate computer through which intranet and extranets are connected.
Note : Extranet is basically the external internet (private) network furnished by the ISP’s to its users . Whereas an intranet is essentially the restricted internet network put in place for the educational/MNC’c to give its users limited access .
What Are The Firewall Types Available To Us For Ensuring System Security ? (Design Of Firewall Mechanism)
Following are the types of Firewalls also called design principles of firewall :
- Packet filtering gateways or screening routers
- Stateful inspection firewalls
- Application proxies
- Guards
- Personal firewalls
We will now dive into the details of each of these Firewall types (design configurations) in detail . So lets proceed further :
Packet Filtering Gateway In Firewall Mechanism
It is the most simple and easy way to implement a firewall. Packet filtering is done on the basis of packets source or destination address or based on some protocol type like HTTP or HTTPs.
If the firewall is placed just behind the router then the traffic can be analyzed easily. In the figure below it is shown that how packet filtering gateway can block traffic from network 1 and allow traffic from network 2.
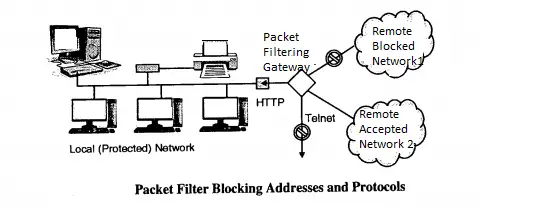
Also, the traffic using the telnet protocol is blocked. Packet filters do not analyze the contents of the packet rather they just check the IP address of the packets .
The biggest disadvantage of the packet filtering gateway is that it requires a lot of detailing to set policies. For example , If port 80 is blocked. If some applications essentially need the use of port 80 then in this case we have to provide all the details of those applications for which port 80 is needed .
Stateful inspection Firewall In Firewall Configuration :
Packet filtering is done one packet at a time. Sometimes attackers may use this technique for their attack. Attacker can split the script of attack into different packets so that the complete script of attack cannot be identified by packet filtering firewall.
To avoid this stateful inspection firewall keeps records of states of the packets from one packet to another. Thus the sequence of packets and conditions within the packets can be identified easily.
Application Proxy Mechanism In Firewall :
Packet filters cannot see inside the packets. From the packet headers, they just get IP addresses for filtering. Application proxy is also known as a bastion host.
Example : A college wants to publish a list of selected students. Then they just want students to read that list. No student can change that list. Moreover, students cannot access more data than the list.
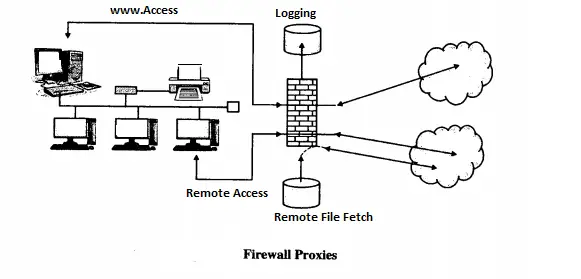
Application proxy helps us in this regard. Here it helps us to check the only the list is displayed on the screen and not more than that. That list should not have any modified contents. Proxies on the firewall can be customized as per the requirements.
Guard In Firewall :
A guard is a kind of complex firewall. It works similarly to a proxy firewall. The only difference is that the guard can decide what to do on behalf of the user by using available knowledge.
It can use knowledge of outside users’ identity, can refer to previous interactions, blocked list etc. Example : In order to increase the speed of the internet a school can set a download limit for the students. A student can download only 20 MB data per day etc
What Are Personal Firewalls ?
For personal use to keep a separate firewall on a separate machine is quite difficult and costly. So personal users need a firewall capability at a lower cost.
An application program that can have capabilities of a firewall can solve this problem. It can screen incoming and outgoing traffic on a single host. Symantec, McAfee, Zone alarm are examples of personal firewalls. Personal firewalls can be combined with Antivirus systems .
What Are The Firewall Configuration Types That Are Available ?
There are mainly a few well-known firewall configuration types present in use today . We will see each of this one by one here . So let’s start :
1. Firewall with Screening Router
The screening router is placed in between the intranet and extranet internet network. It is suitable only if the address screening of the router in a mid way between the two types of network .
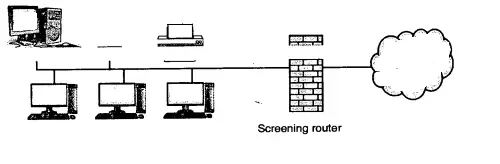
The disadvantage of this configuration is that if the screening router is successfully attacked then the intranet is directly visible.
2. The firewall on Separate LAN
To overcome the problem of the exposure of LAN, a proxy firewall can be installed on its own LAN.
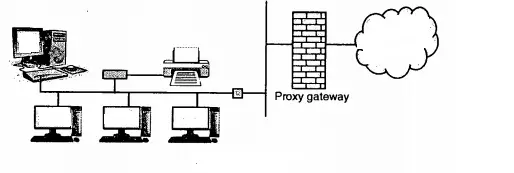
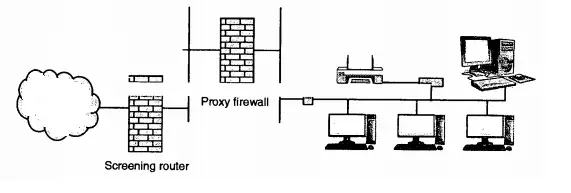
3. Firewall with Proxy and Screening Router
If a screening router is installed behind the proxy firewall, then it ensures the correct address to the proxy firewall. In other words, it is double guard protection. If anyone fails , LAN is not exposed.
I hope you really enjoyed this post about the Firewall types, configuration, and application in detail . Stay tuned for more interesting stuff in this series .

Aric is a tech enthusiast , who love to write about the tech related products and ‘How To’ blogs . IT Engineer by profession , right now working in the Automation field in a Software product company . The other hobbies includes singing , trekking and writing blogs .




