Controlled Access Methods In Dynamic Medium Sharing Techniques Of DLL
In the last post, we have seen the Random Access methods of the medium sharing techniques of the data link layer. Now in this post, we will look into the controlled access methods implemented in the data link layer.
In dynamic medium sharing (controlled access) , the stations consult one another to find which station has the right to send. A station cannot send unless it has been authorized by other stations. The random access approach is simpler to implement and is useful in handling the light traffic.
Here , we will mainly look into the three most important controlled access methods used in transmission medium:
- Reservation System
- Polling System
- Token Passing
Let us understand each one of this one a time :
Reservation System in Dynamic Medium Access Control
In this reservation method, a station needs to make a reservation before sending data. Time is divided into intervals. In each of these intervals, a reservation frame precedes the data frames sent in that interval.
Reservation is a time sharing mechanism. Each multiplexed frame consists of reservation slots. Number of bits per reservation slots is the same as the number of users . One bit is reserved for one user and sets the corresponding bit before transmission.
In this system, each station transmits a single packet at the full rate ‘R’ bps. The transmissions from the stations can be organized into frames of variable length.
If there are ‘N’ stations in any system, there are exactly ‘N’ reservation mini-slots in the reservation frame. Each mini slot belongs to a station.
When a station needs to send a data frame, it makes a reservation in its own minislot. The stations that have made any reservations can send their data frames after the reservation frame.
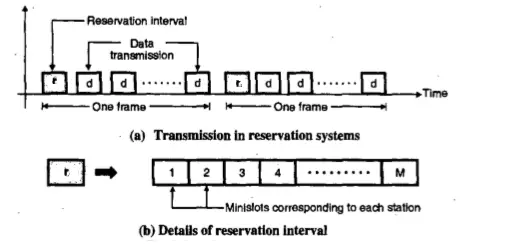
In the above figure, there are ‘M’ mini slots , and the reservation interval is ‘r’ .
These minislots are used by the stations to indicate that they have a packet to transmit in the corresponding frame. The station that wants to transmit packet by broadcasting their reservation bit during the appropriate minislot.
All the stations will listen to the reservation interval, and then determine the order in which packet transmissions in the corresponding frame would take place.
The basic reservation system can be improved by using the time division multiplexing scheme. in the improved reservation system, the idle time slots are allotted to the other stations.
As the number of stations (M) become very large, this overhead will become significant. This then becomes a serious problem. This problem can be sorted out by not allocating a minislot to each station and then instead. making the stations to compete for a reservation of minislot by using a random access technique such as ALOHA or slotted ALOHA.
Biggest demerit of this is the extra bits requirement for the reservation process.
Polling Technique in Dynamic Medium Access Control
In this system, the stations access the common medium one by one (by taking turns). At any instant , only one of the stations will transmit into the medium.
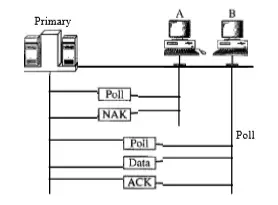
Polling mainly works with topologies in which one device is designated as a primary station and the other devices are secondary stations. All the data exchanges must be done through the primary device even when the ultimate destination is a secondary device.
The primary device controls the link whereas the secondary devices follow its instructions. It is up to the primary device to determine which device is allowed to use the channel at any given time.
When a station finishes its transmitting, then some mechanism is used to pass the right of transmission to another station which wants to transmit next.
The host computer acts as a central controller. It sends control messages which co-ordinate the transmissions from the stations.
The central controller sends a polling message to a particular station. That station sends its message on the shared inbound line. Once this process is over, the station gives a go-ahead message.
If the primary wants to receive data, it will then ask the secondaries if they have anything to send, this is called poll function. If the primary wants to send any data, it tells the secondary to get ready to receive, this is called select function.
In brief, we can say that any secondary station can start frame transmission after the poll command reception. It is a time-sharing mechanism controlled by a primary station.
This is majorly used for the HDLC networks .
Token Passing in Dynamic Medium Sharing Technique
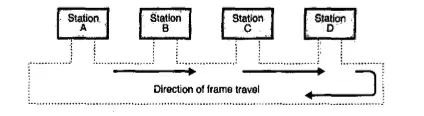
The token is a special frame that is used to authorize a particular station for transmission. In this method, the stations in a network are organized in a logical ring. In other words for a particular station, there is a predecessor and a successor.
The predecessor is the station which is logically before the station in a ring , the successor is the station which is after the station in the ring.
The frames travel in one direction. They come from the predecessor and go to the successor. A token frame is circulated around the ring when no data is being transmitted and the line is idle.
The stations which are ready to send data, will wait for the token. As the token circulates the first’ ready station in the ring will grab the circulating token and transmit one or more frames.
This station will keep sending the frames as long as it has frames to send or the allotted time is not complete. It then passes this token on the ring from which the next ready to transmit station will grab it.
Token management is needed for this access method. Stations have to be limited in the time they can have possession of the token. The token must be monitored in order to ensure it has not been lost or destroyed.
In other words, this is a medium sharing method , wherein multiple users can able to access the same transmission line (medium) without collision.
A token is a 3-byte frame circulated in a given network. Any station can transmit frame after receiving token.
In the next post , we will further look into the channelization techniques implemented in the data link layer for efficient transmission medium sharing. Stay tuned..

Aric is a tech enthusiast , who love to write about the tech related products and ‘How To’ blogs . IT Engineer by profession , right now working in the Automation field in a Software product company . The other hobbies includes singing , trekking and writing blogs .




