Transport Layer – User Datagram Protocol (UDP)
In this post, we will start exploring the two most important protocols used for transporting the data packets from one host to another. We will first start with the simpler of the two protocols i.e. User datagram protocol (UDP). Which is nothing but a connectionless, unreliable protocol.
It provides demultiplexing (using destination port) and error checking on data. In simple words we can say that , there is no need to establish a connection with a host before exchanging data with it using UDP, and further, there is no mechanism for ensuring that data sent is received or not (no acknowledgment) . Data that is sent through this protocol is called a datagram.
If UDP is so powerless, why would any process want to use it? With all the disadvantages there are some vital advantages. UDP is a very basic protocol using a minimum overhead.
If any process wants to send a small message and does not care much about reliability, it can use UDP. Sending a small message by using UDP takes much less interaction(thus much fast) between the sender and receiver than using TCP.
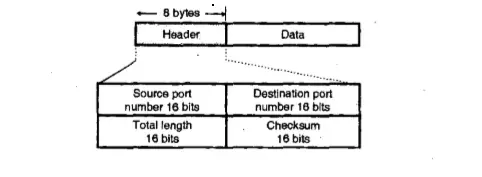
Now let us understand the header field to each datagram sent by using the UDP protocol. UDP adds four 16- bit header fields (8 bytes) to whatever data is sent. These fields are a length field(for datagram length), a checksum field , source, and destination port numbers.
“Port number” simply represents a software port, and not a hardware port . The port numbers mainly identify which protocol module sent (or is to receive) the data. Most protocols generally have standard ports that are generally used for this.
For example, the Telnet protocol generally uses port number 23. The Simple Mail Transfer Protocol (SMTP) uses port 25. UDP or TCP uses the port number to determine which ‘application-Layer protocol should receive the data.
Although UDP isn’t reliable, it is ·still a preferred choice for many applications. It is used in realtime applications i.e. in Net audio and video where, if data is lost, it is better to do without it than send it again out of sequence. Further it is also used by protocols like the Simple Network Management Protocol (SNMP).
Well Known Ports for UDP
The below table shows some well-known port numbers used by UDP. Some of these ports can be used by UDP as well as TCP.
| Port Number | Protocol | Description |
| 7 | Echo | The received datagram is echoed back to sender |
| 9 | Discard | Any received datagram is discarded. |
| 11 | Users | Active users |
| 13 | Daytime | Return the day and the current time |
| 17 | Quote | Return the quote of the day |
| 19 | Charger | To return a string of characters. |
| 53 | Nameserver | Domain Name Service (DNS). |
| 67 | BOOT Ps | This is the server port to download the bootstrap information. |
| 68 | BOOT Pc | This is the client port to download bootstrap information. |
| 69 | TFTP | Trivial File Transport Protocol |
| 111 | RPC | Remote Procedure Call |
| 123 | NTP | Network Time Protocol. |
| 161 | SNMP | Simple Network Management Protocol |
Complete overview of UDP (User Datagram Protocol)
UDP is a connectionless (and unreliable) protocol. Thus no guarantee of sequencing and successful delivery of datagram (data packets) is provided by this protocol. Thus Applications that do not require an acknowledgment of receipt of data, for example, audio or video broadcasting uses UDP.
UDP is also used by applications that typically transmit small amounts of data at one time, for example, the Simple Network Management Protocol (SNMP).
In addition to the data sent, each UDP message contains both a destination port number and a source port number. This makes it possible for the UDP software at the destination to deliver the message to the correct application program, and for the application program to send a reply.
UDP packets are called as Datagram and each of these consists of the below-mentioned fields(8 byte header field)
UDP Datagram Header Fields
The UDP header is divided into the following four 16-bit field :
- Source Port
- Destination Port
- Total Length
- Checksum
Source Port of UDP
This is the port number used by the process running on the source host. Source Port is an optional field, when meaningful, it indicates the port of the sending process.
If not used. a value of zero is inserted. If the source host is the server (a server sending a response), the port number, in most cases, is a well-known port number.
Destination Port of UDP
This port number has been used by the process running on the destination host. It is also 16 bits long . Destination Port has the meaning within the context of a particular Internet destination address.
Length of Datagram
This is a 16-bit field that defines the total length of the datagram packet, header plus data. The 16 bits can define a total length between 0 to 65,535 bytes. This is the size in bytes of the UDP packet, including the header arid data. The minimum length is 8 bytes, the length of the header alone.
There is a field in the IP datagram that defines the total length. There is another field in the IP datagram that typically defines the length of the header.
UDP length = IP length – IP header length
Checksum In Header
Checksum includes three sections: a pseudo header, the UDP header, and the data coming from the application layer. This is used to verify the integrity (i.e. to detect errors) of the UDP header.
The checksum is performed on a “pseudo header” consisting of information obtained from the IP header (source and destination address) as well as the UDP header.
UDP Pseudo Header
The purpose of using a pseudo-header is to verify that the UDP packet has reached its correct destination. The purpose of using a pseudo-header is to verify that the UDP packet has reached its correct destination. The UDP header mainly specifies only the protocol port number.
Thus, to verify the destination, UDP on the sending machine computes a checksum that covers the destination IP address as well as the UDP packet.At the destination machine, UDP software verifies the checksum using the destination IP address obtained from the header of the IP packet that carried the UDP message.
If the checksum agrees, then it has to be true that the packet has reached the intended destination host as well as the correct protocol port within that host.
UDP Operation And Working
UDP implements the common concepts being used in the transport layer to carry the datagram between the host machines. The 4 main functions are :
- Connectionless Service
- Flow control and Error control
- Encapsulation and Decapsulation
- Queuing Mechanism
Connectionless service
One of the features of being connectionless is that the process that uses UDP cannot send a stream of data to UDP and expect UDP to chop them into different related user datagrams. UDP sends each individual datagram , which is totally independent of each other.
All the user datagrams are totally independent of each other even though they are emerging from the same source process and going to the same destination process. These datagrams are not numbered. No connection establishment or connection release (termination) is necessary. Each datagram can follow a different path.
Flow And Error Control
It does not provide any flow control, hence the receiver can overflow with incoming messages(as expected from any unreliable protocol).UDP does not support any other error control mechanism, except for the checksum. The lack of flow control and error control means that the process using UDP should provide these mechanisms.
There are no acknowledgments sent from destination to sender. Hence the sender does not know if the message has reached, lost or duplicated. If the receiver detects any error using the checksum, then that particular datagram is discarded.
Encapsulation and Decapsulation
The UDP encapsulates and decapsulates messages in an IP datagram in order to exchange the message between two communicating processes.
Queuing
This process starts at the client site by requesting a port number from the operating system. In some implementations, both incoming and outgoing queues are created in association with each process. Every process gets only one port number and hence it can create one outgoing and another incoming queue. The queues function only when the process is running.
They are destroyed as soon as the process is terminated. The client process uses the Source port number. mentioned in the request to send a message to its outgoing queue. UDP removes the queue messages one by one by adding the UDP header and delivers them to IP.
Applications of UDP
Despite its unreliability demerit, it can be used in a wide range of application . Some of these are :
It is used for RIP (routing information protocol)
It is used for management processes such as in SNMP.
It is suitable for the processes having inbuilt flow and error control mechanisms, such as TFTP.
It is suitable for multicasting applications.
In the next post, we will dig the next most important protocol of the transport layer i.e. the TCP protocol in detail. So stay tuned.

Aric is a tech enthusiast , who love to write about the tech related products and ‘How To’ blogs . IT Engineer by profession , right now working in the Automation field in a Software product company . The other hobbies includes singing , trekking and writing blogs .




